In this article we look at some of the security threats that have hit Apple’s iOS devices, including XcodeGhost, WireLurker, Masque Attack, the Oleg Pliss ransom case and the SSL flaw. We also discuss what measures you should implement to ensure your device is safe, and we evaluate whether the iPhone and iPad are safe from malware.
According to Apple the iOS platform is completely secure. The company even states that it “designed the iOS platform with security at its core. Keeping information secure on mobile devices is critical for any user, whether they’re accessing corporate and customer information or storing personal photos, banking information, and addresses. Because every user’s information is important, iOS devices are built to maintain a high level of security without compromising the user experience.”
As a result, Apple’s iPad and iPhone are generally considered to be safe and secure devices to use, and many confidently claim that iOS is safer than Android. However, Apple’s iOS platform for the iPad and iPhone hasn’t been without its security breaches and vulnerabilitiies, and nor has iCloud, the cloud storage service which makes it possible to access documents, photos and more on all of your Apple devices.
Read on to find out about:
- The XcodeGhost exploit and what it means to you
- Masque Attack
- WireLurker
- Jennifer Lawrence and the iCloud photo exposure
- The Oleg Pliss ransom case
- The SSL flaw
- How to make sure your iPhone or iPad is secure
- How to update your iPhone to the latest iOS
- Which antivirus program do you need on your iPhone?
- Passwords
- iCloud Keychain
- and more…
The latest security exploits to affect iOS on the iPhone and iPad: What you need to know about XcodeGhost
In the lastest security exploit, which was identified around 20 September, some developers – located in China – have used the incorrect program to create apps for the iOS app store. It is thought that the developers downloaded a fake version of Xcode because it was taking too long to download Xcode from Apple’s own servers, which are hosted in the US. Xcode weighs in at around 3.9GB in total. The Chinese developers were using XcodeGhost rather than Apple’s Xcode.
While the affected apps are Chinese, there are a few popular apps among them such as Angry Birds 2, although Rovio has confirmed that only the Chinese App store version of Angry Birds 2 is vulnerable, and that a fix is coming soon, according to 9to5Mac.
Apparently 39 apps have been affected by the malicious code, according to security firm Palo Alto Networks, there is a full list on 9to5Mac. However, there may in fact be more than 300 apps infected, according to a Chinese security firm who said it found 344 infected apps, writes V3. It seems that only apps purchased from the Chinese App Store are affected though.
Apple began addressing the issue on Sunday after being alerted to the fact that XcodeGhost had been embedded in some apps. “To protect our customers, we’ve removed the apps from the App Store that we know have been created with this counterfeit software and we are working with the developers to make sure they’re using the proper version of Xcode to rebuild their apps,” said Apple.
An affected app could automatically open websites designed to infect the device with a virus, or show pop ups designed to gain personal information from the user in a phishing attempt.
Apple’s walled garden approach to the App Store means it is typically safe. This is the first major breach of the App Store, before this exploit their had only been five instances of affected apps. Android’s open ecosystem, on the other hand, leaves the door open to security issues. Each app goes through a careful review process before Apple allows it into the store. Unfortunately, this time the Xcode malware made its way past Apple’s reviews.
What other security exploits have affected iOS on the iPhone and iPad
2014 was a year of security vulnerabilities and targetting of iOS. First off, a security flaw was discovered in late February 2014 that made it possible that an attacker could intercept your data if you are using an unprotected hotspot, perhaps in Starbucks or an internet café.
Then in late May, some users from the UK, Australia and other countries reported that their iPhones were locked with a message claiming the device was hacked by a person or group named Oleg Pliss who demanded $100 or €100 to unlock it.
Next came news that nude photos of Jennifer Lawrence and around 100 big-name stars including British model Cara Delevigne, Cat Deeley, Kelly Brook, and Rihanna had made their way onto image bulletin board 4chan, at the end of August. Apple claims that the privacy breach was not the result of a compromise of any of the systems used for its iCloud storage service. However, through some means hackers were able to access celebrity photos that were stored in iCloud.
Then in November the first malware with the potential to infect all iPhones and iPads was discovered by security firm Palo Alto Networks. Malware affecting jailbroken devices is nothing new but WireLurker – as the researchers christened it – used a two-stage attack involving USB connections via a Mac or PC, and a glitch in an iOS feature that allows organisations to install their own apps on non-jailbroken iOS devices. While WireLurker installed malicious apps on jailbroken phones and plundered them of personal information – including the device’s phone number and iCloud address book – non-jailbroken phones got off more lightly, with just a benign pirated comic book app invisibly installed on the phone. Basic diagnostic data was also passed to a central command server. Apple has since blocked WireLurker on both iOS devices and Macs but experts suggest that the technique used will give rise to further attacks.
Sure enough, just a week after WireLurker stole the headlines, another iOS 8 malware threat emerged. This threat, known as Masque Attack creates decoy apps that are like those on your iPhone, and these decoy apps attempt to steal your personal information. According to FireEye, who spotted the threat, Masque Attacks can pose much bigger threats than WireLurker.
So, following these recent situations, can Apple maintain its stance that iOS is secure. We examine the various cases that have begged the question of security on the iOS platform, we look at how to make sure your iPhone or iPad is secure (and the problems some people have experienced when updating their device), and we asking whether this mean that Apple’s iOS isn’t secure? Read on to find out…
PART 1: Security threats to iOS devices
We examine the XcodeGhost, WireLurker and Masque Atteck malware, the Olag Pliss ransom case and the SSL flaw. Plus: What really happened in the Jennifer Lawrence nude images leak?
Is XcodeGhost a threat?
39 apps have been affected by the malicious code, according to security firm Palo Alto Networks, however the affected apps are developed in and hosted in China, so it is unlikely that you will be running any of them on your iPhone or iPad, unless you had downloaded them from the Chinese App Store.
For example, while Angry Birds 2 is affected by the exploit, apparently it is only the Chinese App Store version that is affected.
If you are in China, Apple has already removed the affected apps from the App Store.
Was Masque Attack a threat?
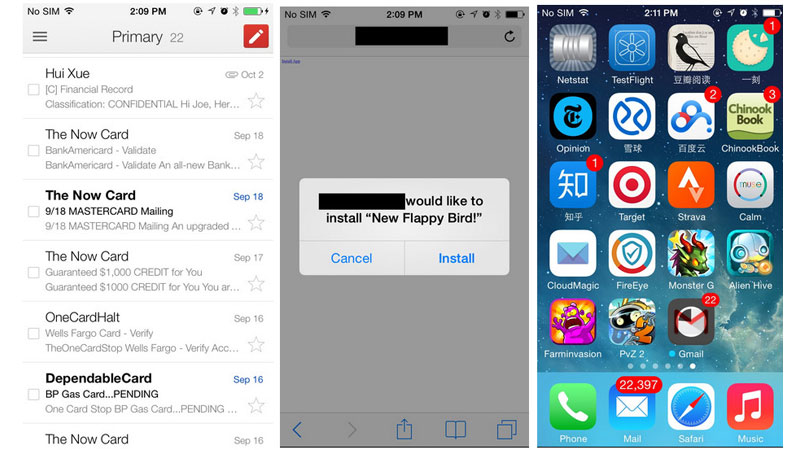
Masque Attack, a threat spotted by FireEye, creates decoy apps that mimic those on your iPhone and steal your personal information.
Apple was able to block WireLurker by blocking enterprise certificate that it was using to install malicious apps, but Masque Attack uses the same bundle identifiers as existing apps instead. According to FireEye: “This vulnerability exists because iOS doesn’t enforce matching certificates for apps with the same bundle identifier.”
To avoid being compromised by Masque Attack, only install apps that come directly from the App Store, don’t click on Install if you see a pop-up on a website or if you see a prompt to install an update to an app like Flappy Bird. Also, if iOS displays an alert that an app is from an Untrusted App Developer tap Don’t Trust and uninstall it.
At its worse the malware could replace Gmail or banking apps with a fake apps that would steal your data you give it.
FireEye said: “We verified this vulnerability on iOS 7.1.1, 7.1.2, 8.0, 8.1 and 8.1.1 beta, for both jailbroken and non-jailbroken devices. An attacker can leverage this vulnerability both through wireless networks and USB.”
Apple has released a statement to iMore, claiming that Masque Attack isn’t really a flaw and that it is unaware of anybody who has been affected.
Because the attack relies on someone actually responding to a dodgy link and downloading an app from somewhere other than the App Store, having ignored a warning about downloading malicious apps, Apple is confident that it has adequate barriers in place to stop people being affected by this particular malware.
However, the best barrier would be to make it impossible to install an app from somewhere other than the App Store, or a company’s own servers or secure-website if it is an in-house app.
Was WireLurker a threat?
WireLurker was a Trojan that was inserted into pirated Mac OS X software, such as popular game titles, as well as within simple Windows executables that promised to install pirated apps on a user’s iOS device.
Notably, although WireLurker infected iOS devices, it wasn’t malware in the traditional sense in that one iOS device did not spread the infection to another. WireLurker could only delivered via a USB connection to a Mac or Windows computer following the download of dodgy software offered on various Chinese websites. The infected software was downloaded over 415,000 times making WireLurker possibly the biggest outbreak of iOS malware yet detected.
Windows users got off lightly because the version of WireLurker used was older and so buggy that it was essentially useless. It also targeted only jailbroken devices.
The version of WireLurker infecting Macs was significantly more sophisticated. It infected other apps on the user’s computer to ensure it was kept running, and installed startup scripts. After grabbing some diagnostic details about the Mac, which it sent to a command server (since closed down), it added an invisible background process that waited for USB connections to iOS devices.
If a user attached a jailbroken device then WireLurker used components of the Cydia jailbreak system to grab personal details, such as the user’s iCloud address book and the device’s phone number, and upload them to the command server. It then infected apps on the device and inserted a handful of other malicious apps.
If a non-jailbroken device was attached, which accounts for the majority of iOS devices in use today, WireLurker silently installed a comic book app on the user’s device. Adding third-party apps via USB should be impossible because of the requirement that they’re digitally signed, which usually happens upon purchase via the official App Store (and which is why iTunes can restore apps to your device). However, WireLurker subverted the enterprise provisioning system that allows organisations to install their own apps on the iOS devices of their employees. This requires a security profile to be installed within the Settings app but the hackers behind WireLurker were able to hide this within the app itself so that it was installed when the app was first run. Users had to click Continue on a dialog box but there was no warning a malicious app might be being installed. Users were sure to run the app when they first spotted it in order to discover what it was.
Aside from the nasty Mac infection, which can be cleared-up using a tool created by the security researchers, the good news is that the app installed on non-jailbroken devices was benign. It was probably more of a test to see if the procedure was possible.
Had an infection taken place the existing security measures within iOS – such as the sandboxing of apps – would have blocked nearly all malicious activity. However, WireLurker has exposed significant flaws within iOS with regard to USB connections and enterprise provisioning that Apple will no-doubt address soon.
What happened in the Jennifer Lawrence nude photos case?

Jennifer Lawrence and around 100 big-name stars including British model Cara Delevigne, Cat Deeley, Kelly Brook, and Rihanna that made their way onto image bulletin board 4chan, at the end of August. The news has lead to some uncertainty about just how secure iCloud is, and what you should do to make sure that the same thing doesn’t happen to you.
First things first, if you aren’t a celebrity chances are nobody is interested in any photos of you. According to Apple these photos were stolen from iCloud in a “very targeted attack”, targetted at celebrities. The hackers then asked for payment in bitcoin to view the photos, some of which were claimed to be fake by the celebrities involved.
Apple said in a statement that: “After more than 40 hours of investigation, we have discovered that certain celebrity accounts were compromised by a very targeted attack on user names, passwords and security questions, a practice that has become all too common on the Internet.”
The company insists that the privacy breach did not stem from a compromise of any of the systems used for the cloud storage service. Apple said: “None of the cases we have investigated has resulted from any breach in any of Apple’s systems including iCloud or Find my iPhone.”
Earlier reports had suggested that a flaw in iCloud was responsible for the hack, but Apple says that none of the cases it has looked into were tied to any vulnerability in the company’s systems.
Apple is working with law enforcement on the matter. The FBI is also investigating.
Read: How to prevent naughty pictures appearing on the web
What happened in the Oleg Pliss ransom case?
Back in May 2014 some people in Australia, the UK, and elsewhere had their Apple ID accounts compromised and their iOS devices held to ransom via Apple’s Find My iPhone service.
Apple’s Find My Phone feature allows iPhone, iPad and Mac owners to remotely lock and track their devices if they’re lost or stolen. A custom message can be displayed on the lockscreen when the feature is activated. In late May, users reported that their iPhones were locked with a message claiming the device was hacked by a person or group named Oleg Pliss who demanded $100 or €100 to unlock it.
Apple said at the time that the incidents were not the result of iCloud being compromised and hinted that password reuse across multiple online accounts might be the cause of the hijackings.
BY mid June, Russian authorities revealed that they had arrested a man and a teenaged boy from Moscow under suspicion that they compromised Apple ID accounts and used Apple’s Find My iPhone service to hold iOS devices for ransom.
It’s not clear if the two Moscow residents, aged 16 and 23, were behind the Oleg Pliss attacks, but the crime referred to in the press release the Russian Ministry of Interior issued to announce the arrests was of a similar nature to the iPhone ransom attacks.
The two allegedly compromised email accounts and used phishing pages and social engineering techniques to gain access to Apple ID accounts. They are then accused of using the Find My Phone feature to lock the associated devices and send messages to the owners threatening to delete data unless the ransom was paid.
Another technique involved placing advertisements online that offered to rent an Apple ID account with access to a lot of media content. Once users accepted the offer and linked their devices with that account, the attackers then used the Find My Phone feature to hijack them, Russian authorities said.
What was the SSL flaw in Apple’s iOS
In February 2014, Apple issued updates to iOS 7 to protect against the security flaw. We recommend that users install the updates.
The SSL problem was with Apple’s implementation of a basic encryption feature that shields data from snooping. Most websites handling sensitive personal data use SSL (Secure Sockets Layer) or TLS (Transport Layer Security), which establishes an encrypted connection between a server and a person’s computer. If an attacker intercepts the data, it is unreadable.
However, iOS’s validation of SSL encryption had a coding error that bypassed a key validation step in the web protocol for secure communications. As a result, communications sent over unsecured Wi-Fi hot spots could be intercepted and read while unencrypted, potentially exposing user password, bank data, and other sensitive data to hackers via man-in-the-middle attacks. They could also supply fake data that makes it appear an authentic web service has been cryptographically verified.
There are also security risks in Mac OS X. Read more about them here: Do Macs get viruses?
In the case of the SSL flaw, the danger is mitigated somewhat since an attacker must be on the same network as the victim. However, you could be open to attacks if you are using a shared network and someone is snooping on that network. This could be someone in your local Starbucks.
Secured Wi-Fi networks, such as home and business networks with encryption enabled, are not affected.
Read about how to keep your social networking private here.
Apple sent a notification of the iOS 7.0.6 update but if you haven’t updated be sure to go to Settings > General > Software Update. You can find the information here.
If you are running iOS 6 you also need to update. Apple has provided iOS 6.1.6 – but this is only available for the iPhone 3GS, much to the annoyance of those who have refused to update to iOS 7. More on that below…

PART 2: Does this mean my iPad and iPhone aren’t safe? How can I make them secure?
Given these examples, should we be concerned about the safety of our iOS devices? How can we ensure that our iPhone and iPad are safe from malicious threats?
How to make sure your iPhone or iPad is secure and safe from WireLurker and other malware
Make sure you keep your iPhone up to date with the latest updates. It may be necessary to install an iOS update to ensure that there was no chance of someone snooping on your activity.
To avoid malware infections such as WireLurker, never attach your device to a computer or even a USB charger unless you’re 100% sure it’s safe. Remember that infections on a Mac or PC are likely to be invisible to the user.
Additionally, never jailbreak your phone because – quite simply – it undoes all the good work Apple has done in securing iOS.
Never use pirated software (or software that promises to install pirated iOS apps), and keep iOS updated too, so that you keep ahead of the jailbreaking exploits that are used by hackers to infect devices. Read: Should you jailbreak an iPhone: Is jailbreaking good for an iPhone or iPad? Is jailbreaking safe? The pros and cons of iOS jailbreaking
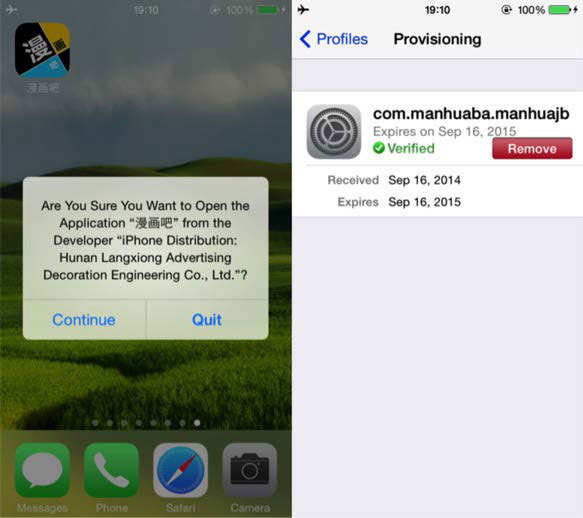
If you suspect you’ve been infected by WireLurker or a similar malware, open the Settings app and then tap General > Profiles. If you’re infected you’ll see an entry here that you didn’t install. Tapping it will offer the chance to remove it (although Apple has already revoked the profile used in WireLurker).
Bear in mind that some apps such as the Cloak VPN app install their own profiles here, as do some Wi-Fi providers. However, you should already know about these, having okayed their installation.
How did the celeb photos hack happen?
Reports initially suggested the iCloud photo leak might have been the result of hackers taking advantage of a flaw in the Find My iPhone service that was said to allow an attacker to try an unlimited number of passwords until the right one was found.
TheNextWeb reported that it had discovered the script that was used to hack into the celebrity accounts on the software site GitHub. That report claimed the script used a flaw in Find My iPhone to crack the passwords for the accounts using “brute force” – in other words the software was able to repeatedly enter the most popular passwords approved by Apple until it hit on the right one. Users would have been unaware that their accounts were compromised.
However, Apple says the hack wasn’t the result of an iCloud vulnerability or a breach in Find My iPhone, but rather a targeted attack where hackers sniff out user names, passwords, and answers to security questions. As Apple says, targeted attacks on specific users are commonplace. For example, Wired editor Mat Honan had his iCloud account hacked back in 2012.
Another suggestion as to how these compromising celebrity photos were acquired was that it could have been through an email phishing attack. The theory is that celebrities could have been tricked into entering their usernames and passwords on a fake login page. We wonder if celebrities are really that silly, although if the email was claiming to be about their nomination at the Baftas or Oscars then anything is possible.
Why were hackers able to get nude celebrity photos?
If you ever lose your iPhone, you may be surprised to find that when you sync up a new iPhone with your iCloud account your old photos appear on the device. As long as you, sensibly, use iCloud to back up the data on your phone when you get your new phone and sync it with the backup you will recover your photos.
Apple also offers a service where the last 1000 photos you take are sucked up into the cloud in an PhotoStream that can be viewed on all your Apple devices including iPad, iPhone, and Mac. This is a handy way to view and save images to a different device.
However, the side effect of these handy services is that your photos are in the cloud and anyone who gains access to your iCloud account could gain access to them. Even if you delete a photo on your iPhone it will remain in your iCloud photo stream until you delete it from that service. Read more about Photo Stream here.
There are various ways a hacker could accessed those photos. They could sync a device using the Apple ID, or they could use software that will access and recover an iPhone iCloud back up, for example.
The iPhone isn’t the only phone to saves photos to the cloud. Android phones saves photos to Google+ and Microsoft’s Windows Phone saves to OneDrive.
How can I stop people getting hold of my photos?
Your phone may only hold photos of your dog or children but it is wise to exercise some caution regardless. In the wrong hands any of your information could be used to nefarious means.
There are a few ways you can make sure that nobody can access the photos on your iPhone and in iCloud. We show you how to completely disable photo sharing to iCloud here, but there is no need to be quite so drastic, as we said above, it’s actually a useful feature.
The three steps for better security are as follows:
1) Choose a secure password. As we explain in this feature about how to chose a strong password, a good password will contain upper and lowercase letters, punctuation, a number and be 8-14 characters long.
2) Use a unique password for every service you access. Most people use the same password for every online service they use which is a danger because once that one password is discovered then all your accounts are vulnerable.
3) Luckily if you have trouble remembering too many password there are services that will generate passwords for you and enter them on your behalf when you need them. You only need to remember one password with a password generator such as 1Password.
4) You can also use Apple’s iCloud Keychain to suggest secure passwords – but make sure you use a password to access your Mac and a passcode for your iPad and iPhone. Read more about setting up Apple’s iCloud Keychain here.
5) Avoid opening and don’t respond to phishing emails (even if you think it’s funny). And definitely don’t click on any links or download any documents that are attached. Note that many phishing emails will appear to have come from friends whose email accounts have been hacked. Follow this advice about phishing emails.
6) If you take a photo and don’t want it to stay in iCloud delete it from your Photo Stream. In the Photos app, go to My Photo Stream select the image and delete. This will remove the photo from any devices connected to your photo stream.
7) Make sure that you use two-factor authentication whenever it is offered. Two-factor authentication adds an extra layer of security besides your username and password. This second layer of authentication involves receiving a security code on your iPhone or other device, which you have to enter in order to access your account. This means that even if someone managed to get hold of your password, if they don’t have access to your phone to get that second security code, they can’t log in to your account. Read: How to set up two factor authentication on iPhone.
8) Make sure that you have good answers to your security questions – not answers anyone could easily guess. And make sure you remember what those answers are!
Update your devices
Make sure you always update your devices to the latest version of the operating system, Apple endeavours to fix flaws as soon as possible.
Updating the software isn’t always as simple as it should be. In the past some people have found that they were unable to install the update that would protect their iPhone. For example, the iOS 7.0.6 update caused some iPhones or iPads to be bricked. Actually calling these devices bricked isn’t necessarily correct, it appears that the firmware update has been interrupted.
Some of these users had attempted to update their iOS device on the move via 3G or 4G rather than over a WiFi network. After the update the iPad or iPhone has required a connection to iTunes before it can restart. Users are asked to “Connect to iTunes”. Should you encounter the same issue with an update there is an Apple Support Community that addresses this iPhone bricking issue, but we outline the steps below:
1. First connect your iPad or iPhone to a power outlet – either to your Mac or plug it into the wall. It is possible that your device ran out of battery when you were updating. You may want to leave it for a few minutes to charge so that you can establish whether that was the problem.
2. Reset your device: hold down the power button and the home button simultaneously. Eventually you should see the Apple logo and the device will boot up (it can take time so be patient, but if its ten minutes there’s probably something wrong!)
3. Restore your device. Beware – this will wipe all the data from your device, so make sure you have a back up first. To restore your iPad or iPhone, first plug it into your Mac and open iTunes. Now click on the name of your iPad or iPhone in the left hand menu and click Restore. This will restore your iPhone or iPad with the latest version of the iOS operating system.
4. Restore from back up: presuming you have a recent backup you will be able to restore your device either via iTunes or over iCloud. It may take an hour or more to restore so be patient (again).
Why you should update your iPad/iPhone OS, and what to do if you can’t
When the SSL flaw happened some people were angry that while Apple has released iOS 6.1.6 for iPhone 3GS and iPod touch (4th generation) users, it was not possible to update a newer iPad or iPhone running iOS 6 device.
We imagine that exactly the same thing could happen now that iOS 9 has been launched. If you still haven’t updated to iOS 9 because you don’t have enough space, you can update using iTunes – read how to upgrade your iOS without deleting anything here.
When the SSL flaw happened, there were people who had refused to update to iOS 7, perhaps because it would have caused their device to slow down. Users complained: “My iPhone 5 gives me no option to upgrade to any iOS other than 7.0.6.”

Unfortunately it was not possible to update a newer device that is running iOS 6 to iOS 6.1.6 if it was eligible for the iOS 7 update.
At the time we even tried doing so in iTunes, but, as you can see, from this screen shot the iOS 6.1.6 update is not available for these devices.

If you don’t want to update to iOS 7.0.6 but don’t want to leave your device open to snooping, how can you avoid the SSL bug without updating to iOS 7?
1. Don’t connect to public Wi-Fi networks.
2. On the Mac it is possible to avoid it by using an alternative browses like Chrome and Firefox, but unfortunately on an iPad or iPhone alternative browsers still use the same underlying web kit and therefore are not safe.
Does this mean that Apple’s iOS isn’t secure?
It’s certainly not going to help the company convince people that they don’t need to be protecting their devices. Many users coming from a desktop environment are already confused about security services for the iPad and iPhone, asking whether they need to install security software on their iPad or iPhone.
Generally these devices are safe because many security features are enabled by default and key features, like device encryption, are not configurable, so users cannot disable them by mistake. Other security measures include low-level hardware and firmware features that protect against malware and viruses.
Apple also approves every third-party application that appears on the iPhone and iPad. As Apple explains: “Unlike other mobile platforms, iOS does not allow users to install potentially malicious unsigned apps from websites, or run untrusted code. At runtime, code signature checks of all executable memory pages are made as they are loaded to ensure that an app has not been modified since it was installed or last updated.”
Another level of protection comes from the device passcode – which means that an attacker with access to your device cannot get access to your data.

Which antivirus program do I need for an iPad or iPhone?
Despite the security threats mentioned above, you don’t need anti-virus software for the iPad and iPhone – not that there is any anti-virus software available for the device. iOS is designed and built to only accept and install software that has been approved by Apple and run through the App Store. As such Apple has pretty much guaranteed that you won’t encounter any malicious software on your iOS device. Similarly security companies complain that Apple will not approve any security focused software for the iPad or iPhone, presumably Apple doesn’t want to give the impression that such software is necessary.
Having said that there are a variety of security-themed apps on the App Store. Security specialist Symantec has a number of apps such as Symantec Mobile Encryption and Symantec Secure Email. These are typically designed to integrate the iPad with an enterprise environment, allowing iOS devices to communicate securely with enterprise servers.
But for the home user, the iPad (and iPhone) is one of the safest computing experiences you can imagine. It’s combination of locked down hardware and software make it more secure out of the box than a Mac or PC with security software installed.
See: VirusBarrier iOS review and Symantec announces new Norton Antivirus tools
What security do I need for iPad and iPhone Safari web browsing?
The Safari web browser in iOS 7 is also protected against malicious software, although you can encounter malicious websites and you are vulnerable to so-called “Phishing” scams (where nefarious people send you emails requesting you to enter account and password details.
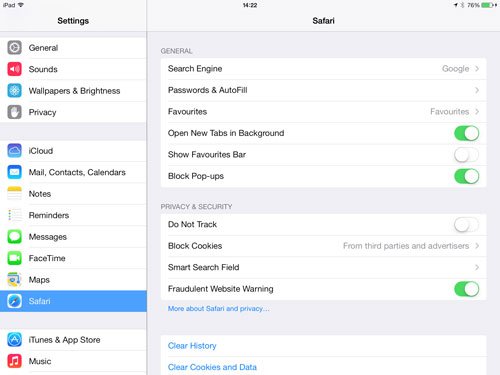
Safari iOS 7 has a “Fraud Warning” service built into it. This is activated by default, but it doesn’t hurt to go to Settings > Safari and double-check that Fraudulant Website Warning is set to On.
Obvioulsy we now know that it is important to update your device to ensure that your safe from man-in-the-middle attacks made possible by the SSL encryption coding error, as discussed at the top of this article. As long as you are running iOS 7.0.6 or iOS 6.1.6 you should be ok.
See: Apple ID phishing scam warning
Is Javascript safe on the iPad and iPhone?
JavaScript is another area where you might want to be extra cautious. While JavaScript offers a number of additional features to websites, there are some concerns that it can be used to launch malicious attacks. It depends on the kind of website you typically browse on an iPad or iPhone. If you look at some of the less salubrious sites you might want to go to Settings > Safari and turn JavaScript to Off.
Are there any iPad/iPhone security risks at all?
The biggest risks with an iPad and iPhone aren’t remote attacks, but up close and personal theft. Somebody either stealing your device or using it when your back is turned.
To protect somebody from accessing your iPad or iPhone without your knowledge be sure to set either a passcode or password.
- Open Settings > General and tap Passcode Lock
- Click Turn Passcode On
- Enter a four digit PIN
- Re-enter the four digit PIN
- Tap “Require Passcode” and ensure it is set to “Immediately”
- Tap Passcode Lock to get back to the Passcode Lock settings
You can use a password instead of a passcode. This will ensure a higher level of security, but you will need to enter the combination of letters and numbers to unlock your iPad or iPhone, so most people stick with the passcode.
- Tap Simple Passcode to Off
- Enter a password (a combination of numbers and letters)
Enable Find My iPad/iPhone
Find My iPhone is an app and service that you can install to locate an iOS if it has gone missing. It also enables you to remotely wipe an iPhone or iPad, or send a message to it in the hope of retrieving a lost iPhone or iPad.
- Click on Settings > Privacy > Location service
- Tap Find My iPad and click it to On
- Open the App Store and Find My iPhone. Install the app.
Open the Find My iPhone app on an iPad or iPhone and log in to see where all your devices are. Note that this service can also be accessed from Apple’s iCloud website.

Saving passwords and credit card details in Safari
The iPad can be used to save your passwords and credit card details. Before doing this it is considered advisable to set up a passcode first, as an additional security measure.
To set up Safari to save passwords follow these steps:
- Tap on Settings and Safari
- Tap Passwords & Autofill
- Tap the Names and Passwords button to turn it on (green)
When you next visit a website in Safari, and enter your name and password, a popup will appear asking if you want to save the password. Tap on Save Password and the password will be stored locally in the iPad.
- Tap Simple Passcode to Off
- Enter a password (a combination of numbers and letters)

To access password details in Safari
- Tap on Settings and Safari
- Tap Passwords and Autofill
- Tap on Saved Passwords
- Tap on a password entry and enter your Passcode
You can now view the Website, Username and Password details on the iPad.
To delete a password from Safari
- Tap on Settings and Safari
- Tap on Passwords and Autofill
- Tap Edit
- Tap the selection circle next to the password you want to delete
- Tap Delete and Delete again in the pop-up window
- Enter your passcode
See also:
Save your credit card details into Safari
If you do a lot of shopping online you might want to enter your credit card details into Safari. They can then be used on a website to make a payment. Follow these steps to add a credit card to Safari
- Tap on Settings and Safari
- Tap on Passwords and AutoFill
- Tap on the button next to Credit Cards
- Tap on Saved Credit Cards
- Tap on Add Credit Card
- Fill out the Cardholder, Numbers, Expires and Description and tap Done
When you are using a website and it requests your credit card information you can use the Autofill option in a pop-up window to fill in the information automatically. Note that you will still need your CVV (Card Verification Value) number to make a purchase. This is the three-digit number on the reverse of most credit cards.
See also:
- How to set up Touch ID fingerprint scanner on iPhone 5s
- How to clear website history and cookies in Safari on a Mac
What is iCloud Keychain?
If you have multiple Apple devices and want to use Safari to save your passwords, then you can use iCloud Keychain to synchronise your passwords from one device to another. So if you enter a password into a website on your iPhone, it will automatically be added to your iPad.
You must have your passcode activated to use iCloud Keychain. Follow these steps to turn on iCloud Keychain
- Tap on Settings and iCloud
- Tap on Keychain and turn on the button next to iCloud Keychain
- Enter your iCloud password and tap on OK
- Move to another computer or device using the same iCloud. On the Mac open System Preferences and iCloud and details next to iCloud
- Enter your Apple ID and Password and click on Allow
Your iPad or iPhone will now have all the usernames and passwords that have been stored on your Mac (and vice versa). You can also do the same thing with your iPhone to sync between all your devices. If you don’t have a Mac you can use an iPhone to authorise the iPad or vice versa, just follow the Notification pop-up and enter your Apple ID and Password on the device.
Your passwords are generally secure on your iPad or iPhone, although you shouldn’t share them with other people. And, of course, anybody who has access to your Passcode as well as your device will then be able to view all your other passwords. So be careful about sharing your iPad and passcode with other people.
We have a lot of faith in Apple to keep our details secure on its server. Apple generally takes security of its back-end systems very seriously. But you will need to enter your passcode to use iCloud Keychain, so it often feels like you’re simply swapping one password for another.
Read about how to protect your privacy on social media sites here.


