You might have heard about WannaCry, ransomware that crippled NHS computers back in May 2017, and the Petya randsomware attack that came at the end of June 2017. It’s been a while since these high-profile cases that were only a danger to PC users, but you might be wondering if, as a Mac user, you should be doing anything to protect yourself from such threats, and how to fix things if you get hit by ransomware.
Here’s everything you need to know about detecting, avoiding and removing ransomware on Macs.
What is Ransomware?
Before we look at the cases of Ransomware on the Mac, we’ll explain what Ransomware actually is. It is a type of malware attack where your files are encrypted against your wishes and a ransom demand tells you to pay a fee if you want to get the files decrypted again.
As referenced above, Ransomware is a concern for Windows users, with WannaCry and Petya being well-known examples on that platform, but is it something to worry about if you use a Mac?
Well, if you use Windows on a Mac you should obviously be as cautious as you would be if you were using Windows on a PC, but if you use macOS Apple has a number of safety measures built in that should protect you, right?
Unfortunately even Macs have been affected by Ransomware attacks, although these are very rare, as you will see if you read on.
This is one of several in-depth Macworld articles dealing with Mac security. If you’re looking for AV buying advice, read our roundup of the Best Mac antivirus and Do Macs get viruses?; general advice can be found in our Mac security tips; and those who think they have been hit by a virus should try How to remove Mac viruses. We also have a full list of Mac viruses here.
Can Macs get ransomware?
Can Macs be infected with ransomware? Has there ever been a case of Mac ransomware?
The answer is yes, but it’s a very rare occurance. There have been a handful of Mac ransomware examples identified by security researchers to date, but not one has led to serious outbreaks and few if any Macs have been affected. However, the list makes interesting reading to learn how a future ransomware outbreak might spread and how it might operate.
ThiefQuest / EvilQuest (June/July 2020)
Malwarebytes highlighted that malicious code was spreading in pirated copies of Little Snitch and other Mac programs on a Russian torrent forum Rutracker.
The program attempts to install itself in several places in the system hides behind names like “com.apple.questd” and “CrashReporter”. If you install it on your computer it will begin encrypting files before showing you a blackmail message asking for $50 bitcoin to decrypt the files. Read more about it here: Mac ransomware could encrypt your Mac.
It’s thought that the ransomware element of this malware might be only part of its purpose – the malware seems to search for certain file types before sending them to a central server before any files are encrypted.
FileCoder / Filezip / Patcher (February 2017)
Security researchers find and identify Filezip ransomware masquerading as “patcher” apps that can be downloaded from piracy sites. Patcher apps are designed to illegally modify popular commercial software like Adobe Photoshop or Microsoft Office so they can be used without purchase and/or a license code.
When the user attempts to use the patcher app, Filezip instead encrypts the user’s files and then places a “README!.txt”, “DECRYPT.txt” or “HOW_TO_DECRYPT.txt” file in each folder listing the ransom demands (0.25 BitCoin; around £335 at the time of writing in May 2017). Notably, like many Windows-based examples of ransomware, Filezip is unable to actually decrypt any files, so paying the ransom is pointless.

KeRanger (March 2016)
Security researchers find and identify KeRanger ransomware within an authorised update for the Transmission BitTorrent client. The first real example of Mac ransomware, this time the ransomware creators have clearly made an effort to create a genuine threat.
KeRanger is signed with an authorised security certificate, so isn’t blocked by the macOS Gatekeeper security system, for example. KeRanger encrypts files and then leaves a README_FOR_DECRYPT.txt file in the directory, in which the ransom demand is made (one BitCoin; around £1,338.62 at the time of writing in May 2017).
However, thanks to fast action by the researchers and also Apple, who immediately revoke the security certificate, KeRanger is halted before it becomes a serious threat. If both agencies hadn’t been quite so quick off the mark, however, it could’ve been a very different story.

Gopher (September 2015) and Mabouia (November 2015)
Two security researchers, working independently, separately create Gopher and Mabouia, two examples of ransomware specifically targeted at Macs. However, both are only proof-of-concept demonstrations, intended to show that fully fledged ransomware on the Mac is entirely possible.
Aside from copies shared with security researchers for them to learn from, neither ever leaves the researchers’ computers, so cannot spread.
FileCoder (June 2014)
Security researchers found and identified FileCoder via the Virus Total virus-scanning website, although by that point FileCoder was already old, having been first detected by the site’s malware scanner two years earlier.
Specifically targeting OS X/macOS, FileCoder is unfinished and not a threat, in that it doesn’t actually encrypt the user’s data. It does display an app window demanding a ransom of €30 (rather cheekily, this is discounted to €20 if a credit card is used instead of PayPal or Western Union).
It’s not known where FileCoder originated, or how it was intended to spread.

FBI scam (July 2013)
For over a decade, website-based ransomware has attempted to extort money from gullible Windows users by “locking” the web browser to a purported law enforcement website. This was always mere smoke and mirrors, however, and could be overcome easily.
But in July 2013 security researchers discovered a similar scam specifically targeting the Mac’s Safari browser. The user was locked to a fake “FBI” webpage via a dialog box that wouldn’t let them leave the site, and a $300 “fine” was demanded to unlock the system.
Quitting the browser was made impossible. If the user force-quit Safari, the ransomware page simply reloaded itself next time Safari started.
Apple has since fixed Safari on both Mac and iPhone/iPad so that it’s less easy for browser-based ransomware like this to operate. However, you might still encounter less virulent examples.

Can Macs get WannaCry?
Put simply, no. WannaCry takes advantage of a bug in Microsoft Windows’ network file sharing system, a technology called SMB. Once WannaCry gets onto a single computer on the network – usually because an individual opened a rogue email attachment – it then uses a bug in SMB to inject itself into all other computers on the network that haven’t been patched.
Macs also use SMB as the default network file sharing technology, so you might initially think Macs could be affected too. However, Apple uses its own bespoke implementation of SMB. While this is fully compatible with Microsoft’s version, it doesn’t suffer from the same bugs or security holes, so isn’t affected by WannaCry – or at least not in WannaCry’s current manifestation.
The iPhone, iPad, Apple TV and even the Apple Watch don’t use SMB file sharing, so aren’t even theoretically at risk from WannaCry.
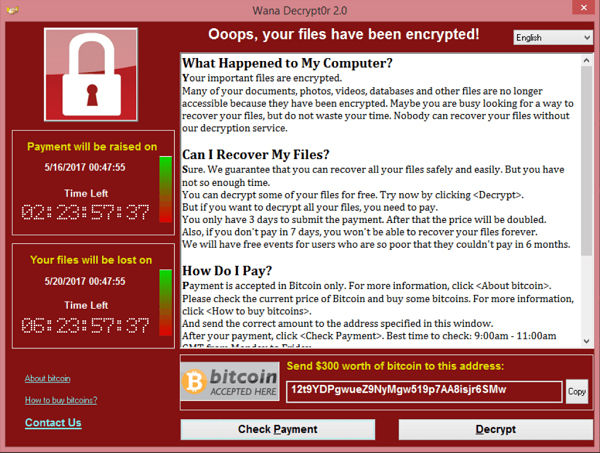
Can Macs get Petya?
Petya is another Ransomware attack, similar to WannaCry, that struck computers in Europe and the US at the end of June 2017.
Petya hit some large firms, and like the earlier WannaCry ransomware attack that affected the NHS in the UK, it spread rapidly to Windows computers on the same network.
Computers are infected due to a vulnerability in Windows for which Microsoft has released a patch.
Most of the antivirus companies have updated their software to protect against Petya.
The Petya ransomware demands that $300 in Bitcoins be paid as the ransom in order to regain access to the computer. However, the perpetrators are thought to be amateurs as the ransom note gives the same Bitcoin address for every victim and only one email address is provided for correspondence – which has of course already been shut down.
The attack may have been targeted at the Ukrainian government rather than as a means to make money.
How to protect a Mac from ransomware
Although at the time of writing there hasn’t been a serious ransomware outbreak on the Mac (or any Apple hardware), security researchers reckon it’s a real possibility.
Speaking on CNBC’s ‘Squawk Box’ programme in the wake of the famous WannaCry ransomware attack, Aleksandr Yampolskiy, CEO of SecurityScorecard, insisted that Apple users are vulnerable to WannaCry-type attacks, even if that specific event affected Windows systems only.
“It happens that this attack is targeting the Windows computers,” he said. “But Apple is absolutely vulnerable to similar types of attacks.”
So, let’s hypothetically assume you’ve been infected. What should you do?
Step 1: Don’t panic
Take your time and avoid kneejerk reactions.
Step 2: Clean up
Use a malware scanner like the free Bitdefender Virus Scanner to search for the ransomware and remove it.
It’s unlikely you’ll be the only person affected by the ransomware so keep an eye on sites like Macworld to learn more about the nature of the ransomware infection. You’ll very likely find specific instructions on how to clean up the infection, if a virus scanner isn’t able to do so.
You might find that a security researcher has found a way to decrypt your files for free, something that happened with the most recent example from the handful of ransomware infections that have been identified on a Mac.
Step 3: Don’t pay
As you’ll see later when we examine the handful of existing ransomware outbreaks affecting the Mac, there’s a good chance paying up won’t actually recover your files!
Step 4: Unplug and disconnect storage
The one example of effective ransomware seen on a Mac so far – KeRanger – also attempted to encrypt Time Machine backups, to try to make it impossible for the user to simply restore files from a backup.
Therefore, upon discovering your Mac has been infected by ransomware you should minimise the possibility of backups becoming encrypted too by immediately unplugging any removable storage like external hard disks, and disconnecting from any network shares by clicking the eject icon alongside their entries in the sidebar of Finder.
Step 5: Install the RansomWhere? app
Consider installing the RansomWhere? app. This free app runs in the background and watches for any activity that resembles the rampant encrypting of files, such as that which takes place during a ransomware attack. It then halts the process and tells you what’s happening. Okay, so some of your files may end up being encrypted, but hopefully not very many.

Step 6: Follow basic phishing protection rules
As with many examples of ransomware and malware, WannaCry initially infected computer networks via a phishing attack. Never open an email attachment you weren’t expecting, even if it appears to come from somebody you know, and no matter how important, interesting or scurrilous it appears to be.
Sept 7: Don’t use dodgy software
The most recent Mac ransomware attempts to spread via “cracked” or patcher apps designed to let you use commercial software for free. Therefore, avoid all dodgy software like this.
Step 8: Always ensure your system and apps are updated
On a Mac you can configure automatic updates by opening the System Preferences app, which you’ll find in the Applications list of Finder, and selecting the App Store icon. Then put a tick alongside Automatically Check for Updates, and putting a tick in all the boxes directly beneath this heading.
Step 9: Install only from official websites
If you suddenly see a pop-up saying one of your browser plugins is out of date, for example, then be sure only to update from the official webpage for that plugin – such as Adobe’s website if it’s the Flash plugin. Never trust the link provided in a pop-up window! Hackers make frequent use of such pop-ups and fake websites to spread ransomware and other malware.
Step 10: Back up frequently, and disconnect
If you have a backup of your files then it matters less if ransomware strikes because you can simply restore. However, the KeRanger ransomware outbreak attempted to also encrypt Time Machine backups, so you might choose to use a third-party app like Carbon Copy Cloner instead to backup your files. Read more: How to back up a Mac
Just backing up your Mac isn’t enough though. To be really safe you should also disconnect your backup drive after the Mac has backed up, that way the drive can’t be encrypted in an attack.
How do I protect my iPhone or iPad from ransomware?
iOS devices like iPhones and iPads were built from the ground-up to be much more secure than Macs, and true ransomware via some kind of malware infection would be extremely difficult to pull-off. There certainly haven’t been any examples so far, or at least on iOS devices that haven’t been jailbroken.
However, iPhones, iPads and even Macs are subject to iCloud hijacking, a type of ransom attack whereby a hacker reuses passwords discovered through one of the many large-scale security breaches in order to log into and take control of a user’s iCloud account. They then change the password and use the Find my iPhone service to remotely lock the iOS device or Mac, sending the user demands for ransom money in order to restore control.
Often they threaten to remote wipe the device or Mac in addition to this. The first such attack of this nature was the Oleg Pliss attack back in 2014.

iCloud hijacking is easily thwarted by setting up two-factor authentication, and you should do so now!
However, regardless of whether an actual ransomware infection is possible, it certainly makes sense to ensure you keep your iPhone or iPad fully updated (read How to update iOS on iPhone or iPad) so as to have the best possible protection against any potential threat. When a new iOS update becomes available a notification will appear alongside the Settings app, and you’ll be able to update by opening Settings then tapping General > Software Update. (Note that there’s no way to configure automatic system updates on iOS.)
Any app claiming to provide antivirus scanning for iOS devices is likely to be dubious at best because all iOS apps are sandboxed, so are unable to scan the system or other apps for malware.
Should I run an anti-virus app all the time?
It might surprise you but Macs already have antimalware built in, courtesy of Apple.
XProtect runs invisibly in the background and scans any files you download as part of the standard file quarantining process. XProtect is updated regularly by Apple with new malware definitions and you can see the frequency of updates by following these steps:
- Open the System Information app by clicking Apple > About This Mac, then clicking the System Report button.
- Select the Software heading in the list at the left, and then the Installations heading beneath this.
- Click the Install Date column heading to sort the list by most recent and look for entries that read XProtectPlistConfigData.
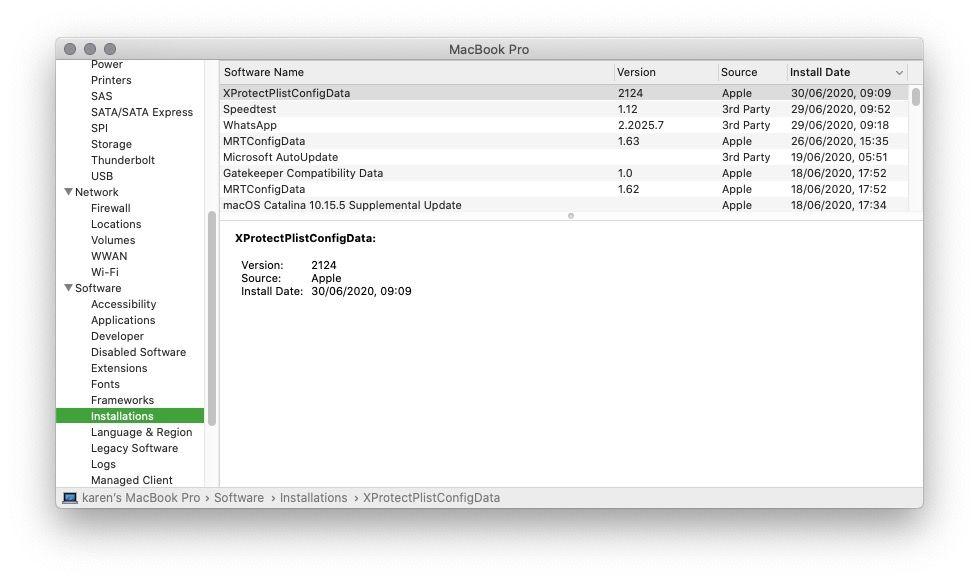
XProtect was how Apple was able to defeat KeRanger, perhaps the most serious Mac-based ransomware threat so far, before it had a chance to become endemic. Additionally, the most recent Mac ransomware, Filezip, has been added to XProtect too.
Combined with other built-in safeguards such as file quarantining and Gatekeeper – both of which stop the user blithely running apps or opening docs they download from strange websites – the Mac is better guarded against ransomware than you might think.
However, there’s certainly no harm in occasionally running an on-demand virus scanner such as Bitdefender Virus Scanner, even if this may well find many false positives in the form of Windows viruses in things like mail attachments. Windows viruses are harmless for Mac users. Read about the best Mac antivirus software here.
